SecTrail MFA Features
|
| Radius Support |
Integration with all devices and applications that support authentication with the Radius protocol (Checkpoint, PulseVPN, F5, Aruba, Cisco, etc.) |
| Workstation Entry |
Windows, Linux |
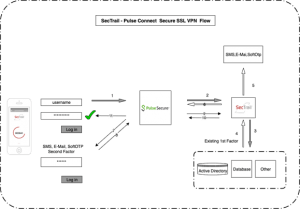
| Remote Login |
VPN, RDP, SSH |
| Authentication Server Support |
Active Directory, LDAP, External Databases |
| Database Support |
MySQL, MS SQL, Oracle DB, PostgreSQL |
| Microsoft Exchange OWA |
Integration with Exchange OWA services through ADFS |
| Microsoft ADFS |
MFA support for all connected applications with Active Directory Federation Services integration |
Authentication Methods
|
| SMS |
Verification with dynamic password that is valid for a limited time via SMS |
| SoftOTP |
Verification without the need for internet access using dynamically generated, time-limited, and single-use keys |
| Email" |
Sending OTP via E-mail |
| QR Kod |
Quick registration opportunity by scanning the QR code with the SecTrail Authenticator mobile application. |
| Hardware Key |
Hardware password generator support for TOTP (Time-Based) and HOTP (Event-Based) |
| Adaptive Authentication |
Assigning different factors to different users (For example, a user who doesn't want to use a mobile application can have their factor sent via SMS.) |
| Customizable Login Method |
Username + (OTP/Notification) |
Multi-Factor Authentication (MFA)"
|
| Computer Protection |
The ability to secure Windows machines with MFA for operating system-level access |
| Offline MFA |
The ability to provide full MFA security on a computer even when offline on both Windows and Linux |
| Data Protection |
Always data encryption |
| MFA Adapter |
API support for third-party applications |
| Prevention of Brute Force Attacks |
Prevention of brute force attacks with dynamic passwords |
Mobile applications
|
| Biometrics |
Active biometric support (FaceID, TouchID, Fingerprint) |
| PIN Lock |
Support for unlocking PIN lock |
| iOS & Android |
Support for both IOS and Android platforms |
| Support for multiple profiles |
Adding multiple profiles to each mobile phone |
Self Servis Portal
|
| Self-registration |
Support for users to create their own profiles in mobile applications |
| Management Panel |
Access log, application access, and device tracking |
Policies and Procedures
|
| General and Group Policy |
Rules and access permissions and restrictions set for each employee in general or specific groups. |
| Location and Region Policy |
Permissions and restrictions for system access from specified locations and regions" |
| Network and IP Security Policy |
Permissions and restrictions for system access from specified networks and IPs |
| Country Policy |
Permissions and restrictions for system access from specified countries |
| Software Policy |
Permissions and restrictions for system access during specified time intervals |
| Blacklist and Whitelist |
To prevent potential attacks, special access restriction and permission lists (IP-browser-country) for access control. |
| API access controls & gateways |
Controlled access to APIs |
| Quarantine |
Lists that provide temporary access restrictions to prevent possible attacks. |
| Device Security Policies |
Implement device security policies based on the security status of mobile phones (encryption, biometrics). |
Emergency Scenarios
|
| Backup |
Support for working with cluster structure. |
| Load balancing |
Being able to respond synchronously to requests from the load balancer with active-active working capability. |
24/7 Support
|
| Uninterrupted support with expert engineers. |