Is Remote Access Safe?
The changing work habits during the pandemic necessitate preventing potential vulnerabilities in the security of both systems and users accessing these systems, in order to ensure the sustainability of the new system.
The weak and predictable passwords used by users to access systems make it easier for hackers carrying out cyberattacks. According to research, the rate of increase in cyber-connected attacks in the United States, exploiting security vulnerabilities of remote workers after the pandemic, has reached up to 250%. (resource) .
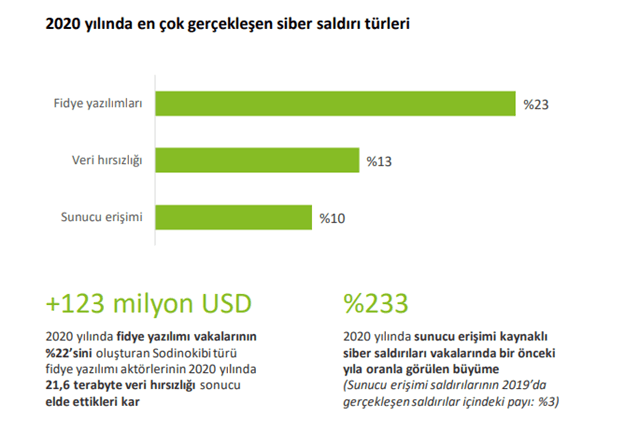
. According to the Turkey Information and Communication Technologies Sector Report by Deloitte and TÜBİSAD in collaboration, the number of records breached due to data leaks in the Cybersecurity domain exceeded 36 billion in 2020, and in the research conducted, it was revealed that 71% of corporate executives believed that remote working increased cyberattacks.
Because of this, the measures that need to be taken in this field are increasing day by day. Identity access and management in cybersecurity have become one of the critical areas that companies plan to allocate the most budget to.
As the pandemic has affected the whole world, it is expected that the MFA market will reach 23.5 billion USD by 2026, both globally and locally, according to research studies

How Can We Ensure Security in Remote Access?
You can prevent end-user vulnerabilities in remote access by using multi-factor authentication methods.
In addition to static passwords, using limited time valid dynamic passwords and instant notifications is an effective method that you can use against unwanted access.
According to trusted reviews multi-factor authentication blocks 99.9% of account hacks related to access vulnerabilities.

What should we pay attention to when choosing a Multi-Factor Authentication solution?
Multi-factor authentication should be positioned as an additional layer of authentication when accessing your systems. In this regard;
- The selected system should be able to integrate with the current topology.
- MFA support being provided without altering the existing topology
- Minimizing integration efforts and change costs
plays an important role.
SecTrail MFA,
- Wide integration support,
- Customizable solutions that can be tailored to fit organization-specific systems
- With its reliable references that it has been serving for a long time,
Our ready-made solution is here to meet your secure access needs, with reliable references that we have been serving for a long time.
Taking a step in the field of MFA for the secure access of your users will protect your company from significant losses. Don't wait too long to position MFA solutions in your company to prevent damages beyond predictable numerical dimensions.









